If you've been working with ClickOnce or VSTO applications, you know that signing them isn't quite like signing a regular executable. We're pleased to announce that Signotaur now handles ClickOnce and VSTO application signing, taking care of the manifest orchestration so you don't have to.
What Makes ClickOnce and VSTO Different?
When you sign a standard executable or DLL, you're dealing with a single file. The process is straightforward: calculate a hash, sign it, embed the signature. One file, one operation.
ClickOnce and VSTO applications are a different beast entirely. These deployment packages consist of multiple files tied together by manifest files that describe the application structure, dependencies, and deployment configuration. The challenge? Everything needs to be signed in a specific order, and those manifests need to be updated with new hash values after each signing operation.
Here's what's happening under the hood:
- Application files get signed first (your assemblies, dependencies, etc.)
- The application manifest (.manifest) needs to be updated with the new hash values of those signed files
- Then the application manifest itself gets signed
- The deployment manifest (.application) needs to be updated with the hash of the signed application manifest
- Finally, the deployment manifest gets signed
Miss a step or do things out of order, and Windows will reject your deployment package. It's tedious and error prone to manage manually, which is exactly why we've automated it.
Certificate Requirements
ClickOnce and VSTO signing requires an RSA certificate with specific characteristics:
- Algorithm: RSA only (ECC/ECDSA certificates are not supported by the ClickOnce/VSTO signing infrastructure)
- Key size: Minimum 2048 bits, though 3072 bits is recommended for better security
- Certificate type: Must be a code signing certificate (Authenticode) from a trusted Certificate Authority
- Key storage: Since June 2023, CA/B Forum requirements mandate that private keys be stored on secure hardware (USB tokens or HSMs)
Signotaur supports all of these requirements, whether your certificates are stored on YubiKeys, SafeNet tokens, other PKCS#11 HSMs, or in the Windows Certificate Store.
The Publisher Name Challenge
Getting the manifests signed is only half the battle. Making your application display the proper publisher name instead of "Unknown Publisher" during installation is notoriously tricky. Even with a properly signed application, several factors can cause Windows to show "Unknown Publisher":
- Certificate chain issues (missing intermediate certificates)
- Publisher name in the deployment manifest not matching the certificate's Common Name exactly
- Whitespace differences introduced during the signing process
- Self-signed or test certificates (which will always show as unknown)
- Certificate not from a trusted root CA
When everything is configured correctly, users see a clean installation prompt with your verified publisher information:
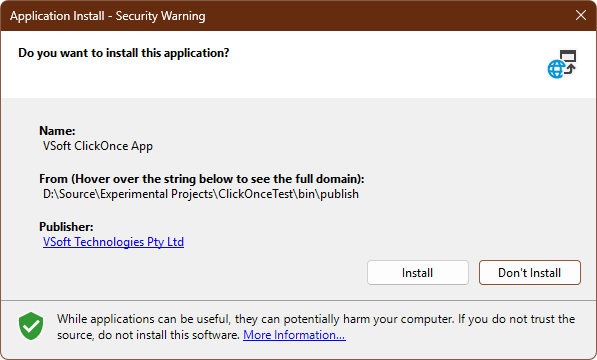
When something's wrong — even if the manifests are technically signed — users see the dreaded "Unknown Publisher" warning:
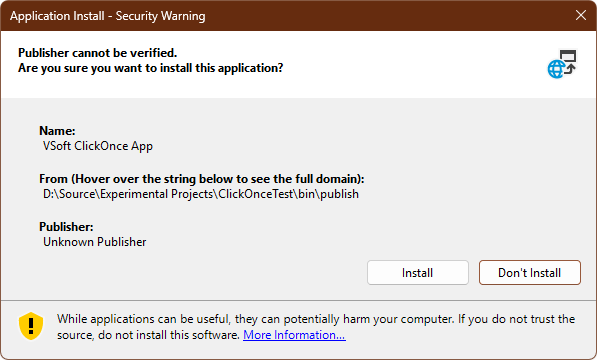
This is why using certificates from trusted CAs and ensuring proper manifest configuration is so important. Signotaur handles all the signing mechanics correctly so all you need to display the verified publisher name is a valid certificate from a publicly trusted Certificate Authority.
Signing Made Simple
To sign a ClickOnce or VSTO application, you only need to point Signotaur at the deployment manifest:
> | SignotaurTool.exe sign -a -s -t --tr --td SHA256 path\to\MyApp.application |
Signotaur will parse the manifest, identify all the files that are part of the application, sign them in the correct order, and update the hash values throughout the manifest chain. Any files sitting in the deployment folder that aren't referenced in the manifest will be ignored, even if they match your file spec. This keeps things clean and ensures only application files get signed.
Command-Line Parameters
We've added a new --application-name parameter specifically for ClickOnce and VSTO deployments. This value appears in the Windows Start menu when users install your application, giving it a proper identity in the system.
The existing --description and --description-url parameters are used to populate the publisher name and support URL in the deployment manifest. This means if you're already using these parameters for other signing operations, your scripts should work with minimal changes.
What This Means for Your Build Process
If you've been juggling multiple tools or scripts to handle ClickOnce and VSTO signing, you can simplify your build pipeline. Signotaur handles the entire process as a single operation, maintaining the correct signing order and manifest updates automatically. This is particularly useful in CI/CD environments where you need reliable, repeatable signing without manual intervention.
The usual benefits of Signotaur apply here: your certificates stay securely on the server, private keys never travel over the network, and the command-line interface integrates cleanly with your existing build scripts.
For detailed command-line syntax and examples, check out the Signotaur documentation. If you run into any issues or have questions about signing ClickOnce or VSTO applications, our support team is here to help.